In the modern era, where information flows through digital channels at the speed of light, the realm of espionage has undergone a profound transformation.
Gone are the days of secret handoffs in dark alleyways and encrypted messages hidden in plain sight. Today, spies are navigating a complex, interconnected world where technology has become both their ally and their adversary.
In this blog, we'll unravel the fascinating world of how spies communicate in the digital age, shedding light on the techniques, tools, and challenges they face in their covert operations.
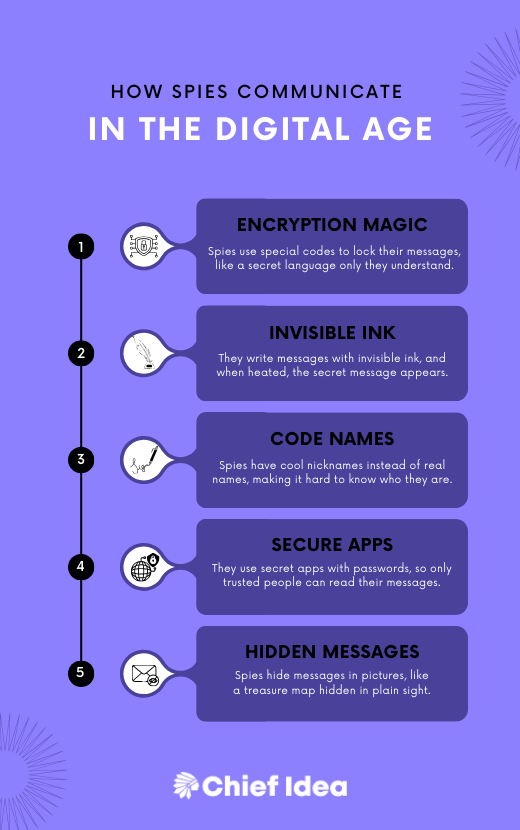
The Digital Evolution of Espionage
The advent of the internet and digital technology has revolutionized espionage in unprecedented ways.
Intelligence agencies around the world have embraced these advancements to enhance their capabilities, making communication faster, more secure, and often nearly impossible to detect.
Here's a glimpse into the modern spy's digital toolkit:
- Encrypted Messaging Apps: In a world where privacy is increasingly under threat, encrypted messaging apps like Signal, WhatsApp, and Telegram have become essential tools for spies. These platforms provide end-to-end encryption, ensuring that only the intended recipient can decipher the messages.
- Secure Email Services: Traditional email is notoriously vulnerable to interception, but secure email services like ProtonMail and Tutanota offer encrypted communication, shielding sensitive information from prying eyes.
- Virtual Private Networks (VPNs): Spies often use VPNs to mask their online presence and location, making it difficult for adversaries to trace their digital footprints.
- Cryptocurrencies: Financial transactions play a significant role in espionage, and cryptocurrencies like Bitcoin offer a level of anonymity that traditional currencies cannot match. Spies can use cryptocurrencies for covert transactions and funding.
- Dead Drops in the Digital Age: While the concept of a physical dead drop still exists, digital dead drops involve spies leaving encrypted files or information in a discreet online location accessible only to authorized parties.
- Cyber Espionage: Intelligence agencies engage in cyber operations to infiltrate enemy networks and extract information. This can include hacking, phishing, and other cyberattacks to gain access to classified data.
- Steganography: Spies may embed hidden messages within seemingly innocuous digital files, such as images or audio recordings. These messages can only be extracted with the appropriate decryption keys.

Challenges in Digital Communication
While digital communication offers significant advantages in terms of speed and security, it also presents unique challenges for spies:
- Digital Traces: Every digital interaction leaves traces, and even with encryption, determined adversaries may find ways to trace communications back to their source.
- Insider Threats: The digital age also brings the risk of insider threats. Spies must be vigilant against double agents or moles within their organizations who might compromise their operations.
- Advanced Cybersecurity Measures: As technology advances, so does the cybersecurity of governments and organizations. Intelligence agencies must constantly adapt and innovate to overcome increasingly sophisticated defenses.
- Ethics and Privacy Concerns: The use of surveillance and cyber operations has raised ethical and legal questions, challenging intelligence agencies to balance national security with individual privacy rights.
Conclusion
In the digital age, the world of espionage has become a high-stakes game played on a global scale.
Spies leverage cutting-edge technology to communicate securely and extract valuable information, all while navigating a treacherous landscape of digital threats and ethical dilemmas.
Understanding how spies communicate in the digital age provides a glimpse into the ever-evolving world of intelligence gathering, where the battle for information supremacy unfolds in the shadows of the cyber world.